Cbc Mac Generation Requires Secret Keys
Posted : admin On 13.12.2020- Enc-Mac (AES CTR+CBC) mixing AES-256 and AES-128 and splitting keys. I'm looking to accomplish a Enc-then-Mac approach using AES-CTR and ECBC-MAC Now ECBC-MAC requires 2 distinct keys, one for the MAC, and one to encrypt the Tag.
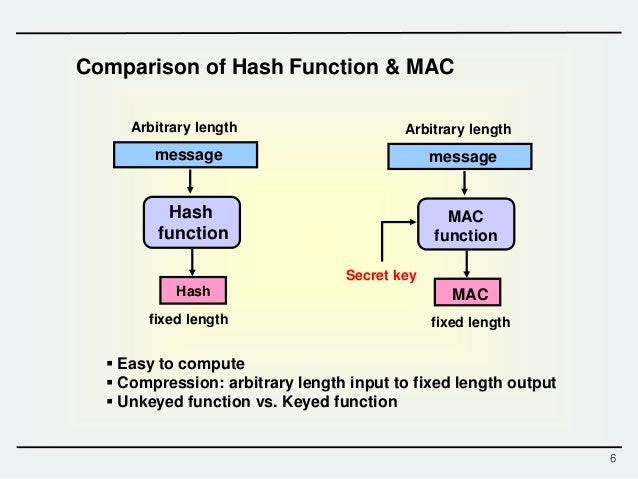
- Aug 29, 2016 MACs are keyed functions that (typically) provide message unforgeability — a very different property. Moreover, they guarantee this only when the key is secret. If you attempt to use CBC-MAC with a non-secret key, it becomes a very bad candidate for anything.
- Cbc Mac Generation Requires Secret Keys Download
- Cbc Mac Generation Requires Secret Keys Lyrics
- Cbc Mac Generation Requires Secret Keys 2017
- Cbc Mac Generation Requires Secret Keys 2
- Cbc Mac Generation Requires Secret Keys Full
MAC Algorithm 5 requires only a single block cipher key setup but it needs a longer internal key. MAC Algorithm 4 applies a special transformation at both the beginning and the end of the processing; this algorithm is recommended for use in applications which require that the key length of the MAC algorithm be twice that of the block cipher.
This article shows how to use standard key derivation functions to derive keys and how to encrypt content using symmetric and asymmetric keys.
Symmetric keys
Symmetric key encryption, also called secret key encryption, requires that the key used for encryption also be used for decryption. You can use a SymmetricKeyAlgorithmProvider class to specify a symmetric algorithm and create or import a key. You can use static methods on the CryptographicEngine class to encrypt and decrypt data by using the algorithm and key.
Symmetric key encryption typically uses block ciphers and block cipher modes. A block cipher is a symmetric encryption function that operates on fixed size blocks. If the message you want to encrypt is longer than the block length, you must use a block cipher mode. A block cipher mode is a symmetric encryption function built by using a block cipher. It encrypts plaintext as a series of fixed size blocks. The following modes are supported for apps:
- The ECB (electronic codebook) mode encrypts each block of the message separately. This is not considered a secure encryption mode.
- The CBC (cipher block chaining) mode uses the previous ciphertext block to obfuscate the current block. You must determine what value to use for the first block. This value is called the initialization vector (IV).
- The CCM (counter with CBC-MAC) mode combines the CBC block cipher mode with a message authentication code (MAC).
- The GCM (Galois counter mode) mode combines the counter encryption mode with the Galois authentication mode.
Some modes such as CBC require that you use an initialization vector (IV) for the first ciphertext block. The following are common initialization vectors. You specify the IV when calling CryptographicEngine.Encrypt. For most cases it is important that the IV never be reused with the same key.
- Fixed uses the same IV for all messages to be encrypted. This leaks information and its use is not recommended.
- Counter increments the IV for each block.
- Random creates a pseudorandom IV. You can use CryptographicBuffer.GenerateRandom to create the IV.
- Nonce-Generated uses a unique number for each message to be encrypted. Typically, the nonce is a modified message or transaction identifier. The nonce does not have to be kept secret, but it should never be reused under the same key.

Most modes require that the length of the plaintext be an exact multiple of the block size. This usually requires that you pad the plaintext to obtain the appropriate length.
While block ciphers encrypt fixed size blocks of data, stream ciphers are symmetric encryption functions that combine plaintext bits with a pseudorandom bit stream (called a key stream) to generate the ciphertext. Some block cipher modes such as output feedback mode (OTF) and counter mode (CTR) effectively turn a block cipher into a stream cipher. Actual stream ciphers such as RC4, however, typically operate at higher speeds than block cipher modes are capable of achieving.
The following example shows how to use the SymmetricKeyAlgorithmProvider class to create a symmetric key and use it to encrypt and decrypt data.
Asymmetric keys
Download windows steam for mac. Asymmetric key cryptography, also called public key cryptography, uses a public key and a private key to perform encryption and decryption. The keys are different but mathematically related. Typically the private key is kept secret and is used to decrypt data while the public key is distributed to interested parties and is used to encrypt data. Asymmetric cryptography is also useful for signing data.
Cbc Mac Generation Requires Secret Keys Download
Because asymmetric cryptography is much slower than symmetric cryptography, it is seldom used to encrypt large amounts of data directly. Instead, it is typically used in the following manner to encrypt keys.
- Alice requires that Bob send her only encrypted messages.
- Alice creates a private/public key pair, keeps her private key secret and publishes her public key.
- Bob has a message he wants to send to Alice.
- Bob creates a symmetric key.
- Bob uses his new symmetric key to encrypt his message to Alice.
- Bob uses Alice’s public key to encrypt his symmetric key.
- Bob sends the encrypted message and the encrypted symmetric key to Alice (enveloped).
- Alice uses her private key (from the private/public pair) to decrypt Bob’s symmetric key.
- Alice uses Bob’s symmetric key to decrypt the message.
You can use an AsymmetricKeyAlgorithmProvider object to specify an asymmetric algorithm or a signing algorithm, to create or import an ephemeral key pair, or to import the public key portion of a key pair.
Cbc Mac Generation Requires Secret Keys Lyrics
Deriving keys
It is often necessary to derive additional keys from a shared secret. You can use the KeyDerivationAlgorithmProvider class and one of the following specialized methods in the KeyDerivationParameters class to derive keys.
| Object | Description |
|---|---|
| BuildForPbkdf2 | Creates a KeyDerivationParameters object for use in the password-based key derivation function 2 (PBKDF2). |
| BuildForSP800108 | Creates a KeyDerivationParameters object for use in a counter mode, hash-based message authentication code (HMAC) key derivation function. |
| BuildForSP80056a | Creates a KeyDerivationParameters object for use in the SP800-56A key derivation function. |
One-key MAC (OMAC) is a message authentication code constructed from a block cipher much like the CBC-MAC algorithm.
Officially there are two OMAC algorithms (OMAC1 and OMAC2) which are both essentially the same except for a small tweak. OMAC1 is equivalent to CMAC, which became an NIST recommendation in May 2005.
It is free for all uses: it is not covered by any patents.[citation needed]In cryptography, CMAC (Cipher-based Message Authentication Code)[1] is a block cipher-based message authentication code algorithm. It may be used to provide assurance of the authenticity and, hence, the integrity of binary data. This mode of operation fixes security deficiencies of CBC-MAC (CBC-MAC is secure only for fixed-length messages).
The core of the CMAC algorithm is a variation of CBC-MAC that Black and Rogaway proposed and analyzed under the name XCBC[2] and submitted to NIST.[3] The XCBC algorithm efficiently addresses the security deficiencies of CBC-MAC, but requires three keys. Iwata and Kurosawa proposed an improvement of XCBC and named the resulting algorithm One-Key CBC-MAC (OMAC) in their papers.[4] They later submitted OMAC1,[5] a refinement of OMAC, and additional security analysis.[6] The OMAC algorithm reduces the amount of key material required for XCBC. CMAC is equivalent to OMAC1.
To generate an ℓ-bit CMAC tag (t) of a message (m) using a b-bit block cipher (E) and a secret key (k), one first generates two b-bit sub-keys (k1 and k2) using the following algorithm (this is equivalent to multiplication by x and x2 in a finite field GF(2b)). Let ≪ denote the standard left-shift operator and ⊕ denote bit-wise exclusive or:
- Calculate a temporary value k0 = Ek(0).
- If msb(k0) = 0, then k1 = k0 ≪ 1, else k1 = (k0 ≪ 1) ⊕ C; where C is a certain constant that depends only on b. (Specifically, C is the non-leading coefficients of the lexicographically first irreducible degree-b binary polynomial with the minimal number of ones: 0x1B for 64-bit, 0x87 for 128-bit, and 0x425 for 256-bit blocks.)
- If msb(k1) = 0, then k2 = k1 ≪ 1, else k2 = (k1 ≪ 1) ⊕ C.
- Return keys (k1, k2) for the MAC generation process.
As a small example, suppose b = 4, C = 00112, and k0 = Ek(0) = 01012. Then k1 = 10102 and k2 = 0100 ⊕ 0011 = 01112.
The CMAC tag generation process is as follows:
- Divide message into b-bit blocks m = m1 ∥ .. ∥ mn−1 ∥ mn, where m1, .., mn−1 are complete blocks. (The empty message is treated as one incomplete block.)
- If mn is a complete block then mn′ = k1 ⊕ mn else mn′ = k2 ⊕ (mn ∥ 10..02).
- Let c0 = 00..02.
- For i = 1, .., n − 1, calculate ci = Ek(ci−1 ⊕ mi).
- cn = Ek(cn−1 ⊕ mn′)
- Output t = msbℓ(cn).
The verification process is as follows:
- Use the above algorithm to generate the tag.
- Check that the generated tag is equal to the received tag.
Implementations[edit]
- Python implementation: see the usage of the
AES_CMAC()function in 'impacket/blob/master/tests/misc/test_crypto.py', and its definition in 'impacket/blob/master/impacket/crypto.py' [7]. - Ruby implementation [8]
References[edit]
Cbc Mac Generation Requires Secret Keys 2017
- ^Dworkin, M J (2016). 'Recommendation for block cipher modes of operation'(PDF). doi:10.6028/nist.sp.800-38b.Cite journal requires
journal=(help) - ^Black, John; Rogaway, Phillip (2000-08-20). Advances in Cryptology – CRYPTO 2000. Springer, Berlin, Heidelberg. pp. 197–215. doi:10.1007/3-540-44598-6_12. ISBN978-3540445982.
- ^Black, J; Rogaway, P. 'A Suggestion for Handling Arbitrary-Length Messages with the CBC MAC'(PDF).Cite journal requires
journal=(help) - ^Iwata, Tetsu; Kurosawa, Kaoru (2003-02-24). 'OMAC: One-Key CBC MAC'. Fast Software Encryption. Lecture Notes in Computer Science. 2887. Springer, Berlin, Heidelberg. pp. 129–153. doi:10.1007/978-3-540-39887-5_11. ISBN978-3-540-20449-7.
- ^Iwata, Tetsu; Kurosawa, Kaoru (2003). 'OMAC: One-Key CBC MAC – Addendum'(PDF).Cite journal requires
journal=(help) - ^Iwata, Tetsu; Kurosawa, Kaoru (2003-12-08). 'Stronger Security Bounds for OMAC, TMAC, and XCBC'. In Johansson, Thomas; Maitra, Subhamoy (eds.). Progress in Cryptology – INDOCRYPT 2003. Lecture Notes in Computer Science. Springer Berlin Heidelberg. pp. 402–415. CiteSeerX10.1.1.13.8229. doi:10.1007/978-3-540-24582-7_30. ISBN9783540206095.
- ^'Impacket is a collection of Python classes for working with network protocols.: SecureAuthCorp/impacket'. 15 December 2018 – via GitHub.
- ^'Ruby C extension for the AES-CMAC keyed hash function (RFC 4493): louismullie/cmac-rb'. 4 May 2016 – via GitHub.
External links[edit]
Cbc Mac Generation Requires Secret Keys 2
- RFC 4493 The AES-CMAC Algorithm
- RFC 4494 The AES-CMAC-96 Algorithm and Its Use with IPsec
- RFC 4615 The Advanced Encryption Standard-Cipher-based Message Authentication Code-Pseudo-Random Function-128 (AES-CMAC-PRF-128)
- OMAC Online Test