Generate 256 Bit Aes Key Openssl
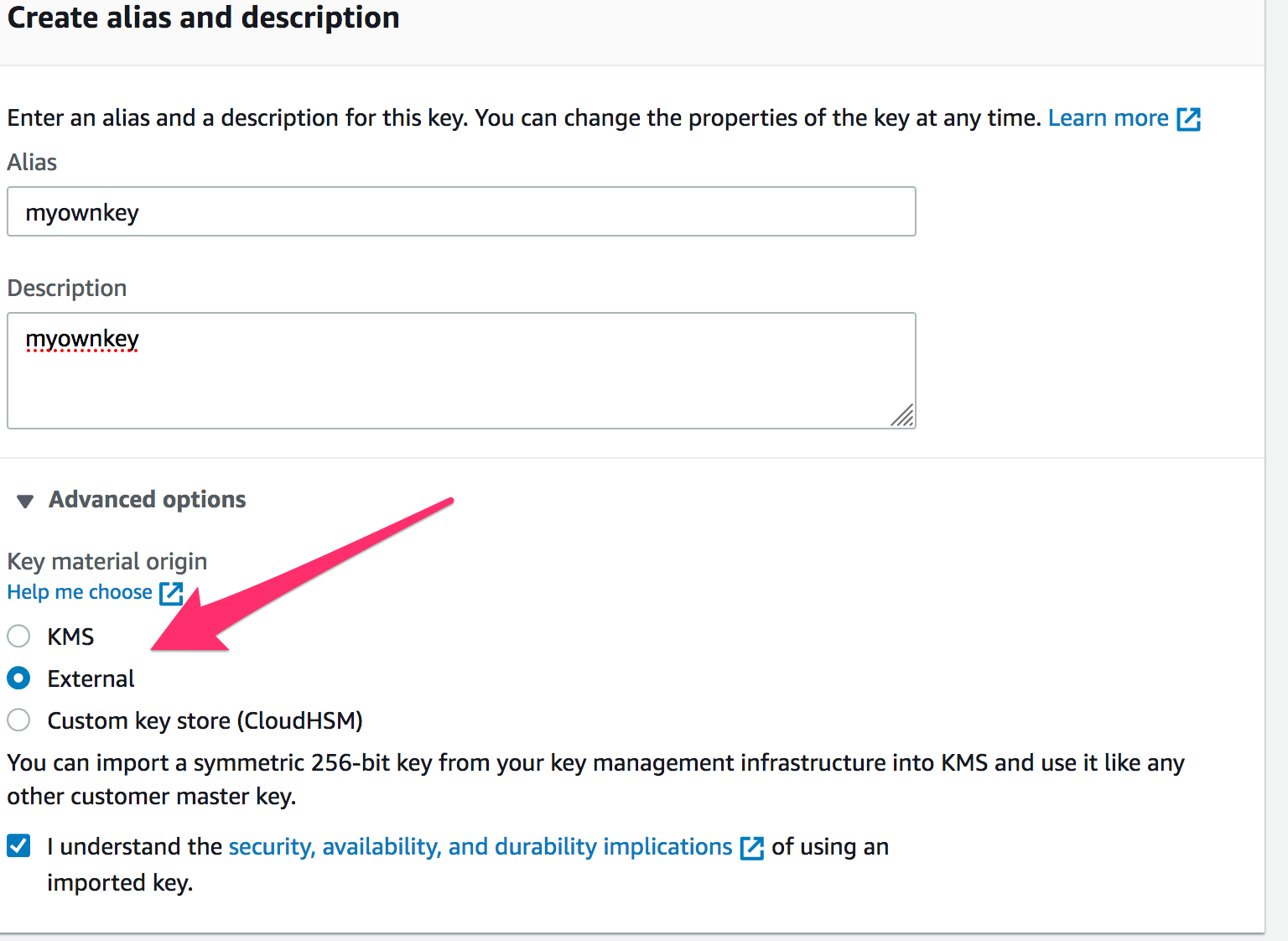
Posted : admin On 14.12.2020To use OpenSSL to generate binary key material and encrypt it for import into AWS KMS. Use the following command to generate a 256-bit symmetric key and save it in a file named PlaintextKeyMaterial.bin. $ openssl rand -out PlaintextKeyMaterial.bin 32.
| <?php |
| // DEFINE our cipher |
| define('AES_256_CBC', 'aes-256-cbc'); |
| // Generate a 256-bit encryption key |
| // This should be stored somewhere instead of recreating it each time |
| $encryption_key = openssl_random_pseudo_bytes(32); |
| // Generate an initialization vector |
| // This *MUST* be available for decryption as well |
| $iv = openssl_random_pseudo_bytes(openssl_cipher_iv_length(AES_256_CBC)); |
| // Create some data to encrypt |
| $data = 'Encrypt me, please!'; |
| echo'Before encryption: $datan'; |
| // Encrypt $data using aes-256-cbc cipher with the given encryption key and |
| // our initialization vector. The 0 gives us the default options, but can |
| // be changed to OPENSSL_RAW_DATA or OPENSSL_ZERO_PADDING |
| $encrypted = openssl_encrypt($data, AES_256_CBC, $encryption_key, 0, $iv); |
| echo'Encrypted: $encryptedn'; |
| // If we lose the $iv variable, we can't decrypt this, so: |
| // - $encrypted is already base64-encoded from openssl_encrypt |
| // - Append a separator that we know won't exist in base64, ':' |
| // - And then append a base64-encoded $iv |
| $encrypted = $encrypted . ':' . base64_encode($iv); |
| // To decrypt, separate the encrypted data from the initialization vector ($iv). |
| $parts = explode(':', $encrypted); |
| // $parts[0] = encrypted data |
| // $parts[1] = base-64 encoded initialization vector |
| // Don't forget to base64-decode the $iv before feeding it back to |
| //openssl_decrypt |
| $decrypted = openssl_decrypt($parts[0], AES_256_CBC, $encryption_key, 0, base64_decode($parts[1])); |
| echo'Decrypted: $decryptedn'; |
| ?> |
While Encrypting a File with a Password from the Command Line using OpenSSLis very useful in its own right, the real power of the OpenSSL library is itsability to support the use of public key cryptograph for encrypting orvalidating data in an unattended manner (where the password is not required toencrypt) is done with public keys.
- We want to generate a 256-bit key and use Cipher Block Chaining (CBC). The basic command to use is openssl enc plus some options: -P — Print out the salt, key and IV used, then exit.k or -pass pass: — to specify the password to use.aes-256-cbc — the cipher name.
- This article discusses how to generate an unencrypted private key and public certificate pair that is suitable for use with HTTPS, FTPS, and the administrative port for EFT Server. (To generate an encrypted key/certificate pair, refer to Generating an Encrypted Private Key and Self-Signed Public Certificate.) General Information.
- In 42 seconds, learn how to generate 2048 bit RSA key. And then what you need to do to protect it. In 42 seconds, learn how to generate 2048 bit RSA key. And then what you need to do to protect it. You can generate a public and private RSA key pair like this: openssl genrsa -des3 -out private.pem 2048. That generates a 2048-bit RSA key pair.
- Mar 12, 2020 Use the OpenSSL command-line tool, which is included with InfoSphere MDM, to generate AES 128-, 192-, or 256-bit keys. The madpwd3 utility is used to create the password.
- What hash function does OpenSSL use to generate a key for AES-256? I can't find it anywhere in their documentation. $ touch file $ openssl aes-256-cbc -nosalt -P -in file enter aes-256-cbc encryp.
- You have a certificate with a 4096 bit RSA key. There is no sense is going higher than that. Which symmetric encryption will be chosen by SSL depends only on what the server/client support, not on the key size of the certificate. You need to fix the server config, not the certificate.
The Commands to Run
Generate a 2048 bit RSA Key
You can generate a public and private RSA key pair like this:
openssl genrsa -des3 -out private.pem 2048
That generates a 2048-bit RSA key pair, encrypts them with a password you provideand writes them to a file. Avg secure vpn serial key 2018. You need to next extract the public key file. You willuse this, for instance, on your web server to encrypt content so that it canonly be read with the private key.
Export the RSA Public Key to a File
This is a command that is
openssl rsa -in private.pem -outform PEM -pubout -out public.pem
The -pubout flag is really important. Be sure to include it. /generate-debug-and-production-api-key-google-map-android.html.
Next open the public.pem and ensure that it starts with-----BEGIN PUBLIC KEY-----. This is how you know that this file is thepublic key of the pair and not a private key.
To check the file from the command line you can use the less command, like this:
less public.pem
Do Not Run This, it Exports the Private Key
Aes 256 Encryption Key Generator
A previous version of the post gave this example in error.
openssl rsa -in private.pem -out private_unencrypted.pem -outform PEM
The error is that the -pubout was dropped from the end of the command.That changes the meaning of the command from that of exporting the public keyto exporting the private key outside of its encrypted wrapper. Inspecting theoutput file, in this case private_unencrypted.pem clearly shows that the keyis a RSA private key as it starts with -----BEGIN RSA PRIVATE KEY-----.
Visually Inspect Your Key Files
It is important to visually inspect you private and public key files to makesure that they are what you expect. OpenSSL will clearly explain the nature ofthe key block with a -----BEGIN RSA PRIVATE KEY----- or -----BEGIN PUBLIC KEY-----.
You can use less to inspect each of your two files in turn:
less private.pemto verify that it starts with a-----BEGIN RSA PRIVATE KEY-----less public.pemto verify that it starts with a-----BEGIN PUBLIC KEY-----
The next section shows a full example of what each key file should look like.
The Generated Key Files
The generated files are base64-encoded encryption keys in plain text format.If you select a password for your private key, its file will be encrypted withyour password. Be sure to remember this password or the key pair becomes useless.
The private.pem file looks something like this:
Openssl Generate Aes Key
The public key, public.pem, file looks like:
Protecting Your Keys
Depending on the nature of the information you will protect, it’s important tokeep the private key backed up and secret. The public key can be distributedanywhere or embedded in your web application scripts, such as in your PHP,Ruby, or other scripts. Again, backup your keys!
Remember, if the key goes away the data encrypted to it is gone. Key generator free download for windows 7 ultimate. Keeping aprinted copy of the key material in a sealed envelope in a bank safety depositbox is a good way to protect important keys against loss due to fire or harddrive failure.
Oh, and one last thing.
If you, dear reader, were planning any funny business with the private key that I have just published here. Know that they were made especially for this series of blog posts. I do not use them for anything else.
Found an issue?
Rietta plans, develops, and maintains applications.
Learn more about our services or drop us your email and we'll e-mail you back.